The scammers here today are called MS Info Services, although they do call you claiming to be from the support department at the real Microsoft.
Their cold call was made to my Google Voice from this number:
800-920-3886
They started the call off by asking me to open event viewer to see all the errors and warnings. The scammer continued by telling me that he needed to connect me to “Microsoft’s secure server” in order to help me fix my computer. After he got connected, he ran Netstat as well as telling me that my IP address and Firewall has been corrupted by outside hackers who are trying to connect to my VM. His explaining went on for close to about an hour before he opened up notepad and started typing what he was going to fix and the plans. I went ahead and decided to go with the lifetime plan and here is where it gets interesting. Instead of copying and pasting all my info from Notepad onto his own computer, he advised me that I would received an invoice in my email and that I needed to complete the information by myself (he said that he was not allowed to have primary control of my computer). Sidenote: maybe they’ve been RAT’ed before?
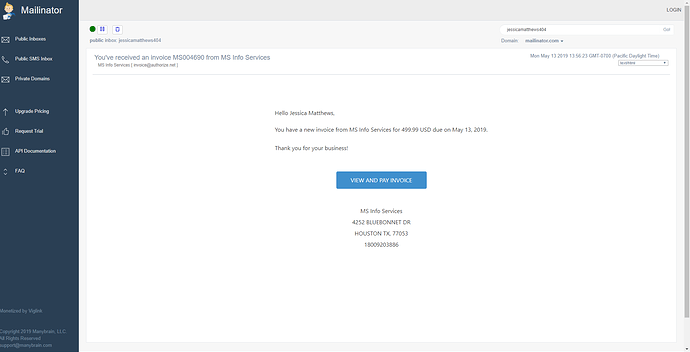
Anyways, here is the Invoice that appeared in my email:
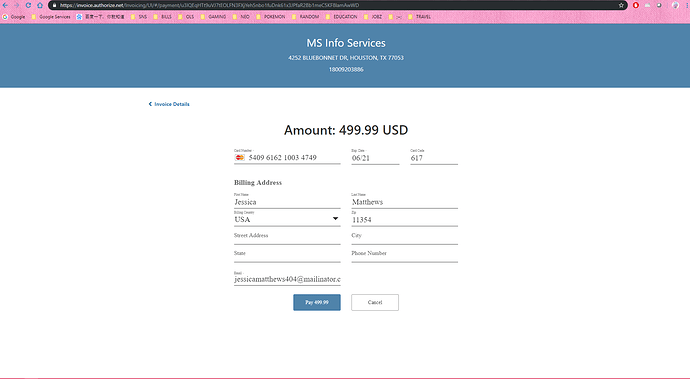
What the button leads to:
Website to the service that provides the payment gateway:
So after 2-3 failed attempts the billing manager told me that I should write a check and send it to the address listed on the invoice. I told him that I would need to run to the bank to get some temporary checks, and the billing manager said that the technician would work on my machine in the meanwhile. So for around 30 mins, I sit in front of my VM and see what the technician does. He opens up Windows Defender and does a scan. After than he pulls up 2 or 3 cmd windows and proceeds to run a scan using different colors. LOL!
After around 30 mins, the billing manager calls me back. I told him that I went to the bank already and that the check is already in the mail. He sounded defeated (likely because I didn’t say that I took a picture) but said okay. After he hung up, he started the file transfer from GoToAssist and started transferring stuff to the desktop of my VM.
After transferring the files, he proceeds to call me again and say that I sent the check to the wrong address.
He told me to send the check to this address instead:
4252 Bluebonnet Drive
Stafford, Texas
77477
I told him that I’d have to go to the bank again so he hangs up. At this point, I decided that I would quickly make a RAT and make the icon to my EXE a picture of a filled out bank check. I compile the rat and in around 30 mins the billing manager calls me back again. I quickly open up GoToAssist and tell him that I’ve taken a picture this time and I transferred the picture to him through GoToAssist. I guess instead of opening it on his PC, he opened it on my PC and then said that it won’t open. I quickly opened up GoToAssist again and sent him the jpeg file this time with the fake check and fake information I filled into the check. This time he opens it on his PC and after a few seconds of silence he figures out that the check looks sketchy. Probably because I didn’t change the account/routing numbers on the bottom. I play dumb and tell him that I don’t know what hes talking about. I then tell him that he needs to give me 10 minutes to call my bank to see what went wrong. I hang up. I notice that the scammer instantly starts deleting stuff that hes already saved to my desktop. At this point, I decided it was a good idea to kill the GoToAssist process since I did RAT my own VM before hand (I wanted to run those batch files, and exe’s before he got a chance to delete them).
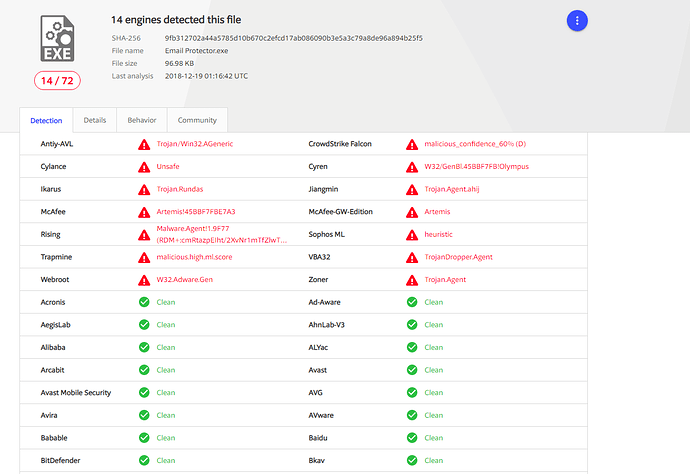
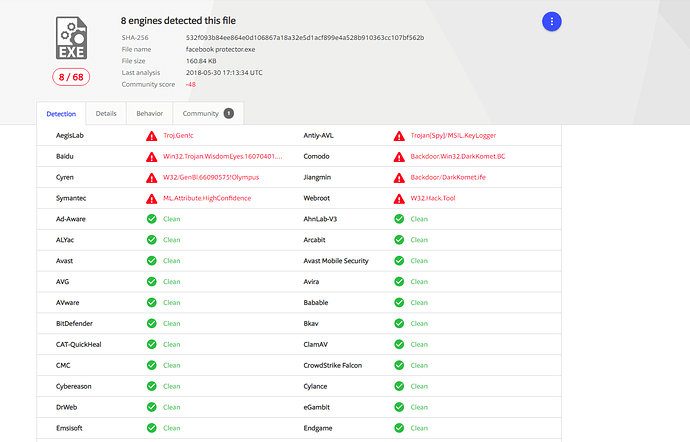
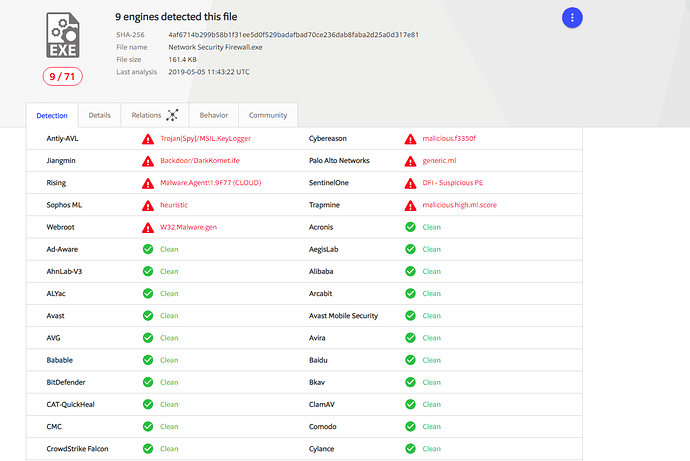
Anyways, here are the results of those Virus Total scans:
In conclusion though, I’d say that this group of scammers were either too dumb or a little smater than most.
As always, thank you for reading and happy scam baiting!