How to Remote Control a Windows VM Without Guest Tools
Existing remote control methods either rely on guest tools running in the VM or some agent process being started on the VM. Neither of these is an ideal solution; the scammer will see guest tools running and starting the agent requires some interaction with the VM.
Our goal is to use standard Windows components to allow an undetectable connection from outside. For that we’re going to use SSH. Basically this will give you access to the terminal from another computer on the same network, without anything showing up on the screen.
Install OpenSSH Server
The official installation guide from Microsoft gives more detailed instructions but in summary the steps are;
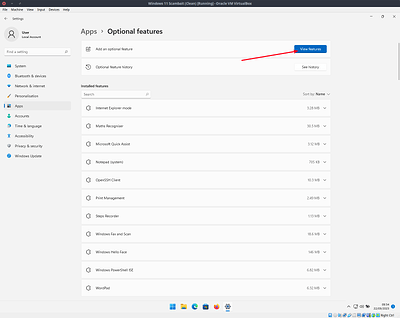
First open system settings and navigate to the list of optional features
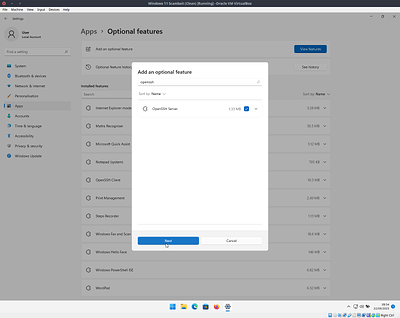
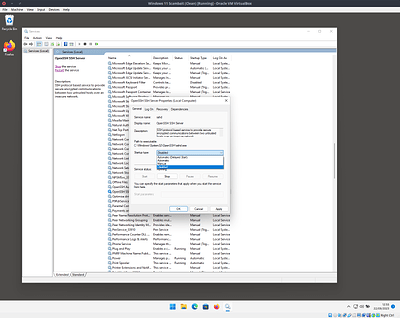
Next search for OpenSSH then select and install it
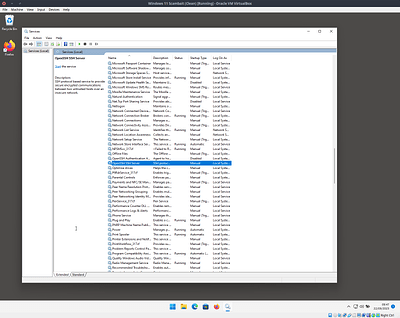
Now we need to make sure the OpenSSH service is disabled - this differs from the official instructions and is explained more and bit further down.
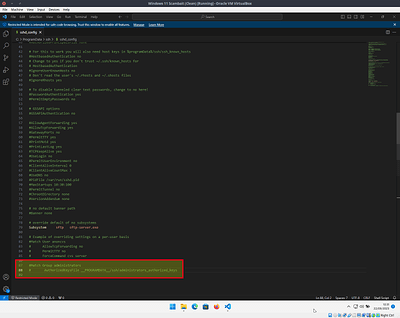
By default Windows overrides some settings for users in the administrator group, open C:\ProgramData\ssh\sshd_config in any editor and comment out the last two lines by adding a # symbol to the start of the line.
Now we’re going to create a scheduled task to start OpenSSH whenever the user logs in. Running it in this way instead of as a service allows interaction with the desktop, so running notepad will pop up a window on the screen instead of it being hidden in the special console session that services run in.
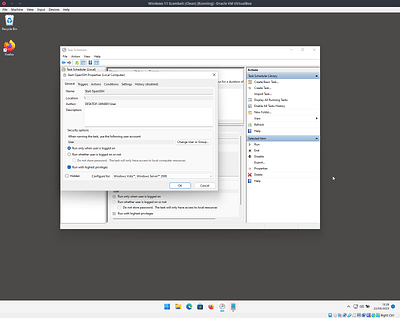
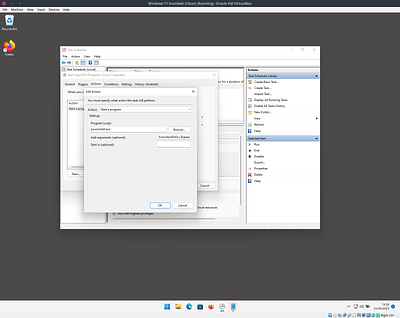
Open up task scheduler and use the “Create Task…” action from the menu on the right
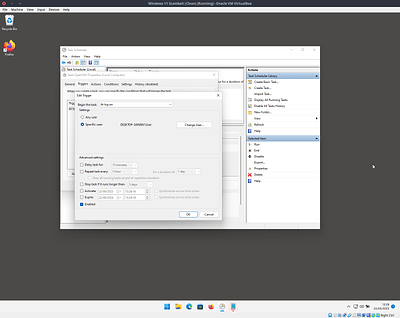
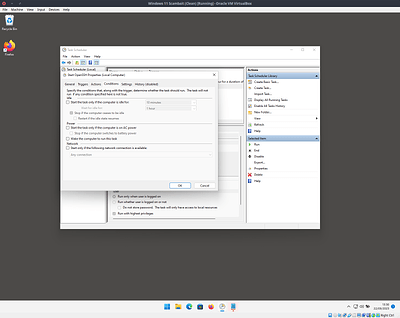
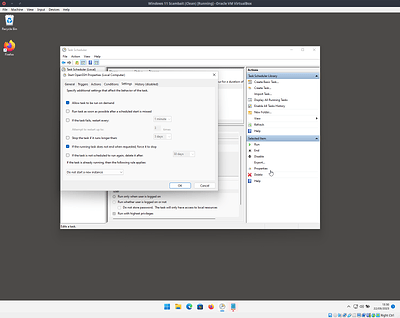
Configure the task as shown in these image
For the action use powershell.exe as the program and -ExecutionPolicy Bypass -WindowStyle Hidden sshd.exe as the arguments.
Now reboot the VM and verify that the process starts, After you login a blue powershell window should appear for half a second or so. You can also check task manager for sshd.exe.
Configure Authentication
SSH can authenticate remote users using shared keys, basically this means you don’t have to enter a password to run commands or copy files.
First you need to create a key on the machine that you’ll be using to connect to the VM - this could either be your host computer or another VM on the same network. I’d recommend using a second VM as a precaution.
I used a Linux VM for the client but a Windows one would work too.
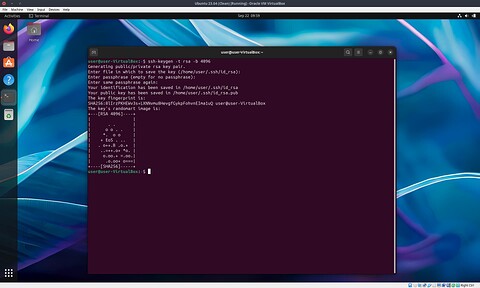
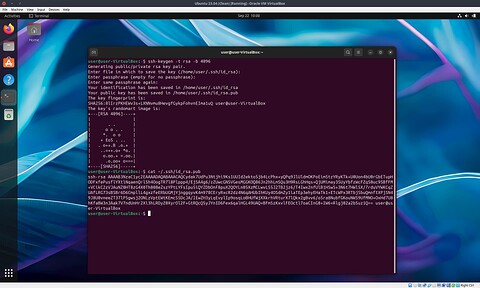
Pop open a Terminal and enter ssh-keygen -t rsa -b 4096, just accept the default options and don’t set a password on the key otherwise you’ll have to type it in every time you connect.
The contents of the ~/.ssh/id_rsa.pub file is your public key, this can be added to a file on any machine running an OpenSSH server to grant you access to it. Never share the contents of the is_rsa (without the .pub extension) file with anyone - that’s basically your password.
Copy this line somewhere for later.
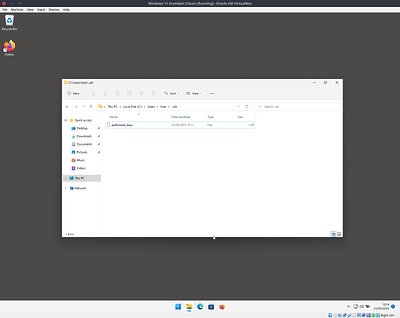
Back on the Windows machine now, create a file to store the authorised public keys at C:\Users\[username]\.ssh\authorized_keys (replace [username] with the default username)
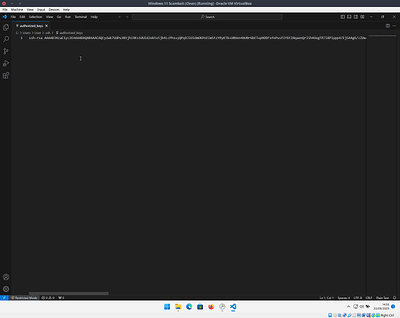
Edit this file and put the contents of the id_rsa.pub file from before on a new line
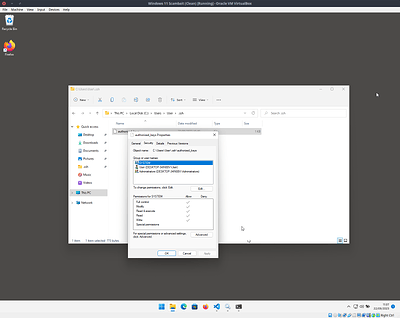
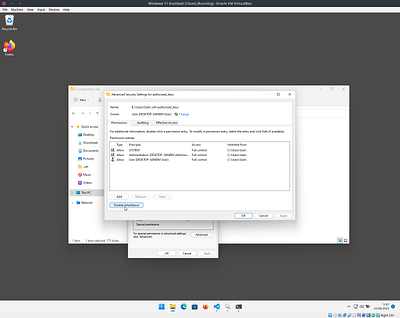
Finally, because Windows is kinda dumb with permissions, you need to edit the security permissions of this file to make sure only you and the system user can access it
Right click on the file then go to the security tab and click the Advanced button
On the new window click Disable inheritance
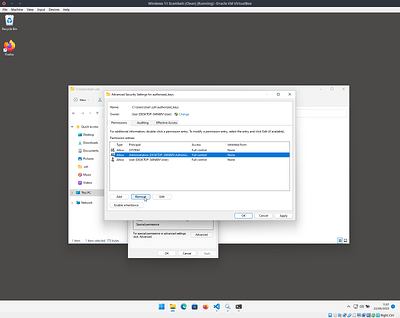
Finally remove the administrator group from the permissions list, leaving only SYSTEM and your user account.
Apply everything and go back to the desktop.
Try it Out
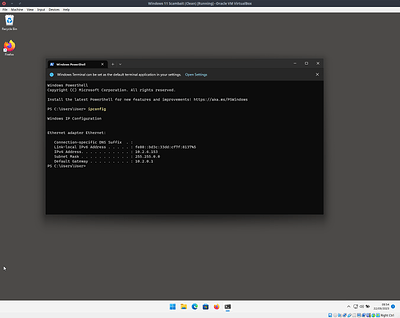
Grab the IP of the VM on your local network
Now use the ssh command to connect to this host from the other machine. The syntax is ssh [remote_user]@[remote_computer] so for me this is ssh [email protected]
The first time you connect to a host you’ll be prompted to accept its identity - just type yes and hit enter.
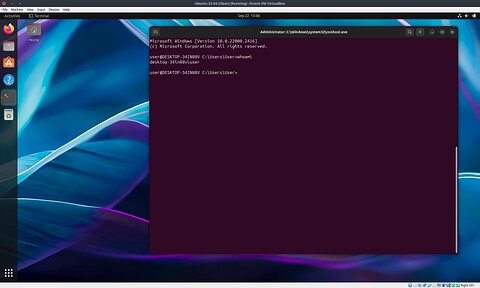
If everything worked out this should drop you in to something that looks a bit like cmd.exe
Entering anything here should behave just as if you entered it in the command prompt on the host. To switch to powershell just enter powershell and hit enter.
And that’s it ![]()
Example Things To Try
Pop open an alert box
msg %username% y u scam bro?
Drop a file on the VM (run this from the Linux terminal, not after connecting)
scp whatever.txt [email protected]:/Users/User/Desktop/file.txt
Open a web page
"C:\Program Files\Mozilla Firefox\firefox.exe" https://techscammersunited.com
Close the browser (thanks for the suggestion @John_Smith )
taskkill /IM firefox.exe
Leave anything else fun below ![]()